Implementing Internet Protocol Security (IPsec) on Cisco routers.
- July 21, 2024
- Posted by: James Majani
- Categories: Cisco, Networking
Basic Concepts.
IPSec is a suite of protocols and services that provide security for IP networks. It is a widely used Virtual Private Network (VPN) technology. IP packets lack effective security mechanisms and may be forged, stolen, or tampered with when being transmitted on a public network, such as the Internet. To solve this problem, the communicating parties establish an IPsec tunnel for encrypted transmission of IP packets. This ensures secure transmission of IP packets on an insecure network, such as the Internet.
IPSec has several standards:
IP Security Protocol
o Authentication Header (AH)
o Encapsulating Security Payload (ESP)
Data Encryption Standard (DES)
Triple DES (3DES)
Diffie-Hellman (D-H)
Message Digest 5 (MD5)
Secure Hash Algorithm-1 (SHA-1)
Rivest, Shamir, and Adelman (RSA) Signatures
Internet Key Exchange (IKE)
Certificate Authorities (CAs
Networking Description.
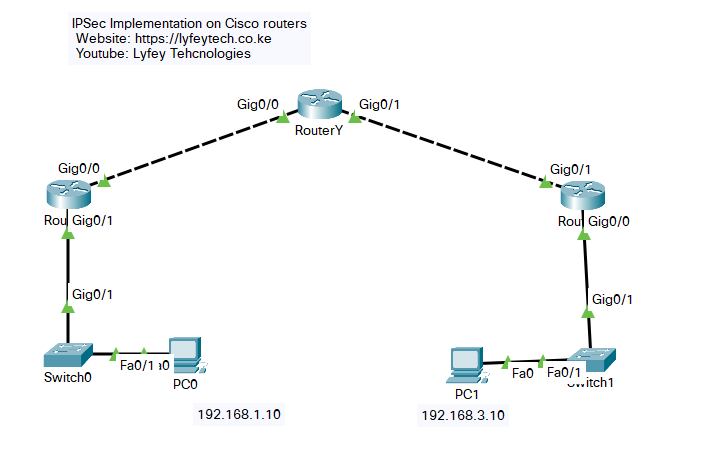
As shown in our topology, HQ router, BRANCH1 routers, are gateways of the enterprise headquarters and branch. The service provider has allocated a public network IP address to each gateway and the gateways can communicate with each other.
The enterprise requires a simple cost-effective mechanism to implement communication between the headquarters and branches through Internet. IPSec tunnels can be established between the headquarters and branches to meet this requirement.
Step 1: Basic configurations.
*******************************************BRANCH_Router
enable
conf t
hostname BRANCH_Router
interface gig 0/0
no shut
ip add 10.0.0.1 255.255.255.252
exit
ip route 192.168.3.0 255.255.255.0 10.0.0.2
int gig 0/1
no shut
ip add 192.168.1.254 255.255.255.0
exit
ip route 192.168.3.0 255.255.255.0 10.0.0.2
ip route 10.0.0.4 255.255.255.252 10.0.0.2
*******************************************ISP_Router
enable
conf t
hostname ISP_Router
int gig 0/0
no shut
ip add 10.0.0.2 255.255.255.252
exit
int gig 0/1
no shut
ip add 10.0.0.6 255.255.255.252
exit
*******************************************HQ_Router
enable
conf t
hostname HQ_Router
int gig 0/1
no shut
ip add 10.0.0.5 255.255.255.252
exit
int gig 0/0
no shut
ip add 192.168.3.254 255.255.255.0
exit
ip route 192.168.1.0 255.255.255.0 10.0.0.6
ip route 10.0.0.0 255.255.255.252 10.0.0.6Step 2: Enable security license for IPsec configuration.
*******************************************BRANCH_Router
enable
conf t
license boot module c1900 technology-package securityk9 (yes)
exit
copy running-configuration startup-configuration
reload
*******************************************HQ_Router
enable
conf t
license boot module c1900 technology-package securityk9 (yes)
exit
copy running-configuration startup-configuration
reloadRun the command “show version ” to check license information.
Step 3: Configure access-list to match interesting traffic.
*******************************************BRANCH_Router
conf t
access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
*******************************************HQ_Router
conf t
access-list 100 permit ip 192.168.3.0 0.0.0.255 192.168.1.0 0.0.0.255Step 4: IPSec VPN configurations.
*******************************************BRANCH_Router
//Configure IPsec ISAKMP policy.
conf t
crypto isakmp policy 10
encryption aes 256
authentication pre-share
group 5
exit
//Configure the preshared key.
crypto isakmp key halloweenkey address 10.0.0.5
//Configure IPSec transform set
crypto IPsec transform-set 1 esp-aes 256 esp-sha-hmac
//Configure crypto map
crypto map IPSEC-MAP 10 IPsec-isakmp
set peer 10.0.0.5
set pfs group5
set security-association lifetime seconds 84600
set transform-set 1
match address 100
exit
*******************************************HQ_Router
//Configure IPSec ISAKMP policy.
crypto isakmp policy 10
encryption aes 256
authentication pre-share
group 5
exit
//configure the preshared key.
crypto isakmp key halloweenkey address 10.0.0.1
//Configure IPsec transform set.
crypto IPsec transform-set 1 esp-aes 256 esp-sha-hmac
//Configure crypto map.
crypto map IPSEC-MAP 10 IPsec-isakmp
set peer 10.0.0.1
set pfs group5
set security-association lifetime seconds 86400
set transform-set 1
match address 100
exitStep 5: Apply the Crypto map to the interface.
*******************************************BRANCH_Router
configure terminal
interface GigabitEthernet 0/0
crypto map IPSEC-MAP
*******************************************HQ_Router
configure terminal
interface GigabitEthernet 0/0
crypto map IPSEC-MAPStep 6: Check IPSec parameters on the routers and Ping the LAN-side of Branch and HQ.
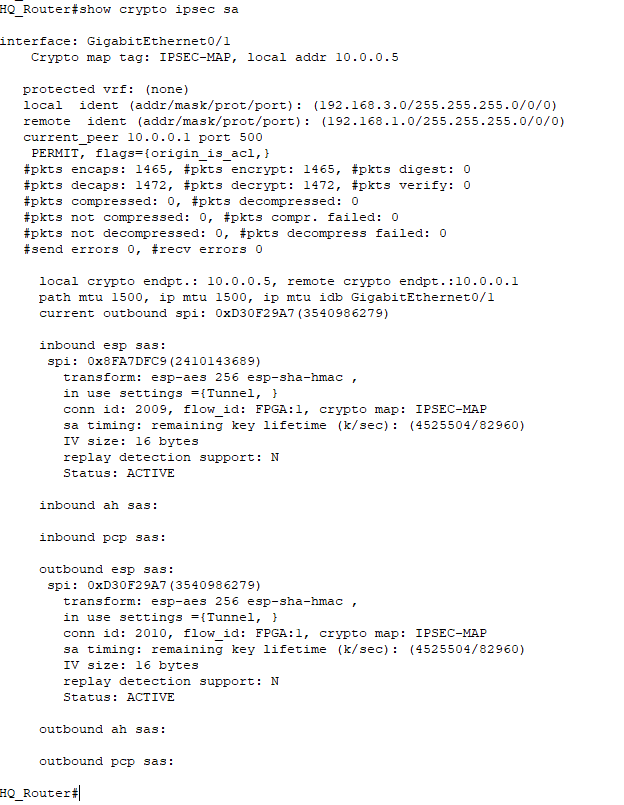
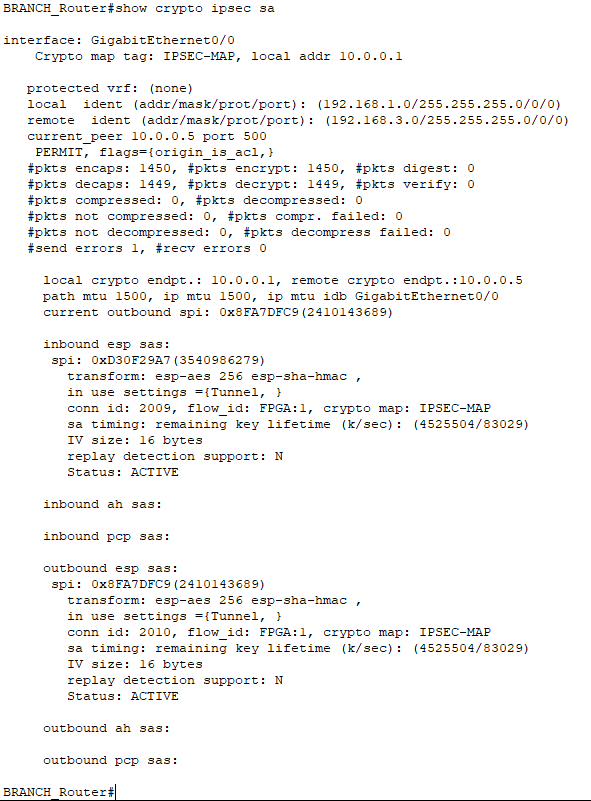
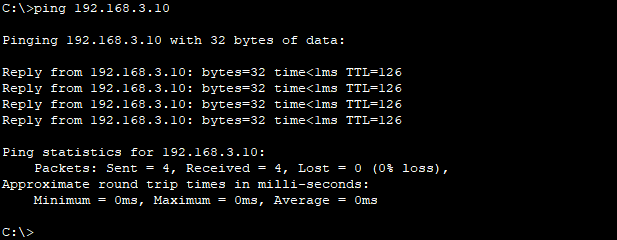
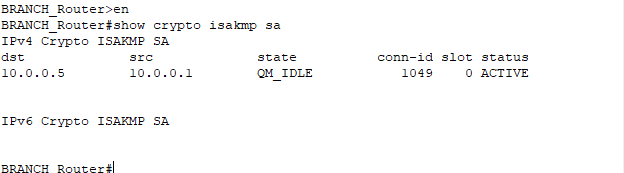
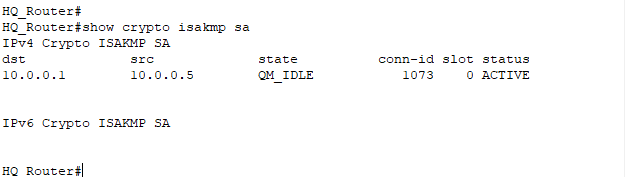

best online thai pharmacy: prozac overseas pharmacy – Sporanox
viagra pharmacy online: mexitil online pharmacy – post haste pharmacy viagra
viagra online singapore VGR Sources purchase 200mg sildenafil
sildenafil coupon: online viagra prescription usa – 150 mg viagra online
50 mg viagra price: buy generic viagra from europe – 20 mg sildenafil cheap
us pharmacy viagra online: order sildenafil 50 mg – where can i get viagra prescription
where to get female viagra: where to buy cheap viagra in usa – can you buy viagra online safely
authentic viagra where can you buy viagra for women viagra soft cheap
viagra pills 100 mg: sildenafil pills from mexico – online pharmacy canada generic viagra
https://vgrsources.com/# price of viagra per pill
viagra brand price: price of viagra 100mg in usa – sildenafil 48 tabs 50 mg price
generic viagra coupon: get a viagra prescription online – buy viagra online fast shipping
generic viagra price uk best over the counter viagra 2017 viagra 100mg canada
average cost of viagra 100mg: VGR Sources – viagra pills over the counter canada
purchasing viagra in mexico: sildenafil without prescription from canada – sildenafil 20mg prescription cost