Running BGP between Cisco routers and the Palo Alto Firewall
- February 16, 2024
- Posted by: Lyfey Technologies
- Category: Networking
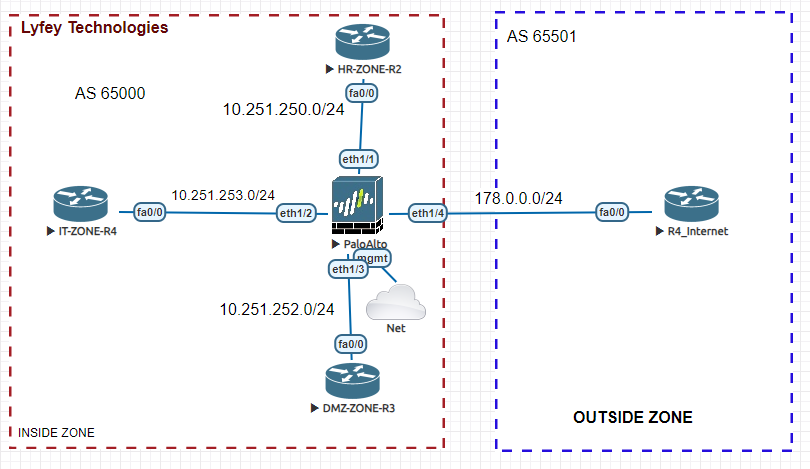
When setting up your network composed of Cisco routers and Palo Alto Firewalls, you have multiple options for achieving communication within your AS and also communication with outside networks. You can use static routes or run dynamic routing protocols like OSPF, RIP, and BGP. In our last article, we demonstrated how to configure OSPF between your Cisco routers and the Palo Alto firewall. Check out the lab simulation on OSPF configuration from this link: Configuring OSPF between Cisco routers and Palo Alto Firewalls
In this article, we demonstrate how to configure BGP for inter-zone communication in a network with Cisco routers and Palo Alto Firewalls.
Step 1: Configure system names, IP addresses, and BGP on the routers.
******************************IT-ZONE-R4
enable
configure terminal
hostname IT-ZONE-R4
interface FastEthernet0/0
ip address 10.251.253.10 255.255.255.0
no shutdown
!
router bgp 65000
no synchronization
bgp log-neighbor-changes
neighbor 10.251.253.100 remote-as 65000
no auto-summary
!
write******************************HR-ZONE-R2
enable
configure terminal
hostname HR-ZONE-R2
!
interface FastEthernet0/0
ip address 10.251.250.10 255.255.255.0
no shutdown
!
router bgp 65000
no synchronization
bgp log-neighbor-changes
neighbor 10.251.250.100 remote-as 65000
no auto-summary
!
write******************************DMZ-ZONE-R3
enable
configure terminal
hostname DMZ-ZONE-R3
interface FastEthernet0/0
ip address 10.251.252.10 255.255.255.0
no shutdown
!
router bgp 65000
no synchronization
bgp log-neighbor-changes
neighbor 10.251.252.100 remote-as 65000
no auto-summary
!
write******************************R4_Internet
enable
configure terminal
hostname R4_Internet
!
interface FastEthernet0/0
description TO_PA_FW_01
ip address 178.0.0.10 255.255.255.0
no shutdown
!
router bgp 65501
no synchronization
bgp log-neighbor-changes
network 178.0.0.0 mask 255.255.255.0
neighbor 178.0.0.100 remote-as 65000
no auto-summary
!Step 2: Run Basic configurations on the Firewall
set deviceconfig system hostname PA01
set deviceconfig system type static
set deviceconfig system timezone Africa/Nairob
set deviceconfig system domain lab.local
set deviceconfig system ip-address 192.168.71.130
set deviceconfig system netmask 255.255.255.0
set deviceconfig system default-gateway 192.168.71.128
set deviceconfig system dns-setting servers primary 8.8.8.8
set deviceconfig system dns-setting servers secondary 1.1.1.1Step 3: Configure interfaces on the PaloAlto Firewall
set network interface ethernet ethernet1/1 link-state up
set network interface ethernet ethernet1/1 comment ZONE_DMZ_1
set network interface ethernet ethernet1/1 layer3 interface-management-profile Ping
set network interface ethernet ethernet1/1 layer3 ip 10.251.250.100/24
set network interface ethernet ethernet1/2 comment INSIDE_ZONE
set network interface ethernet ethernet1/2 link-state up
set network interface ethernet ethernet1/2 layer3 interface-management-profile Ping
set network interface ethernet ethernet1/2 layer3 ip 10.251.253.100/24
set network interface ethernet ethernet1/3 comment DMZ_ZONE2
set network interface ethernet ethernet1/3 link-state up
set network interface ethernet ethernet1/3 layer3 interface-management-profile Ping
set network interface ethernet ethernet1/3 layer3 ip 10.251.252.100/24
set network interface ethernet ethernet1/4 layer3 ip 178.0.0.100/24
set network interface ethernet ethernet1/4 layer3 interface-management-profile Ping
set network interface ethernet ethernet1/4 comment OUTSIDE_ZONE
set network interface ethernet ethernet1/4 link-state upStep 4: Configure a Virtual router and assign the interface to the virtual router.
set network virtual-router VR01
set network virtual-router VR01 interface [ ethernet1/1 ethernet1/2 ethernet1/3 ethernet1/4 ]Step 5: Configure your security zones on the Firewall and assign interfaces to respective zones accordingly
set zone OUTSIDE_ZONE network layer3 ethernet1/4
set zone INSIDE_ZONE network layer3 ethernet1/2
set zone DMN_ZONE1 network layer3 ethernet1/1
set zone DMZ_ZONE2 network layer3 ethernet1/3Step 6: Configure a security policy to allow communication between zones. We allow communication among all zones in our lab simulation.
set rulebase security rules Allow_ALL to any
set rulebase security rules Allow_ALL from any
set rulebase security rules Allow_ALL source any
set rulebase security rules Allow_ALL destination any
set rulebase security rules Allow_ALL source-user any
set rulebase security rules Allow_ALL category any
set rulebase security rules Allow_ALL application any
set rulebase security rules Allow_ALL service application-default
set rulebase security rules Allow_ALL hip-profiles any
set rulebase security rules Allow_ALL action allowStep 7: Configure BGP between your Cisco routers and the Palo Alto Firewall.
set network virtual-router VR01 protocol bgp enable yes
set network virtual-router VR01 protocol bgp router-id 100.100.100.100
set network virtual-router VR01 protocol bgp local-as 65000
set network virtual-router VR01 protocol bgp install-route yes
set network virtual-router VR01 protocol bgp peer-group Out-R1 enable yes
set network virtual-router VR01 protocol bgp peer-group Out-R1 peer R4_Internet local-address ip 178.0.0.100/24
set network virtual-router VR01 protocol bgp peer-group Out-R1 peer R4_Internet local-address interface ethernet1/4
set network virtual-router VR01 protocol bgp peer-group Out-R1 peer R4_Internet peer-address ip 178.0.0.10
set network virtual-router VR01 protocol bgp peer-group Out-R1 peer R4_Internet peer-as 65501
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer HR-ZONE-R2 local-address ip 10.251.250.100/24
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer HR-ZONE-R2 local-address interface ethernet1/1
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer HR-ZONE-R2 peer-address ip 10.251.250.10
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer HR-ZONE-R2 peer-as 65000
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer HR-ZONE-R2 enable-mp-bgp no
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer HR-ZONE-R2 address-family-identifier ipv4
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer HR-ZONE-R2 enable yes
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer IT-ZONE-R4 local-address ip 10.251.253.100/24
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer IT-ZONE-R4 local-address interface ethernet1/2
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer IT-ZONE-R4 peer-address ip 10.251.253.10
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer IT-ZONE-R4 peer-as 65000
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer IT-ZONE-R4 address-family-identifier ipv4
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer IT-ZONE-R4 enable yes
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer DMZ-ZONE0-R3 local-address ip 10.251.252.100/24
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer DMZ-ZONE0-R3 local-address interface ethernet1/3
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer DMZ-ZONE0-R3 peer-address ip 10.251.252.10
set network virtual-router VR01 protocol bgp peer-group Internal_Peering peer DMZ-ZONE0-R3 peer-as 65000
set network virtual-router VR01 protocol bgp peer-group Internal_Peering enable yesStep 8: Verify your BGP peering is up on the Palo Alto firewall and the routers.
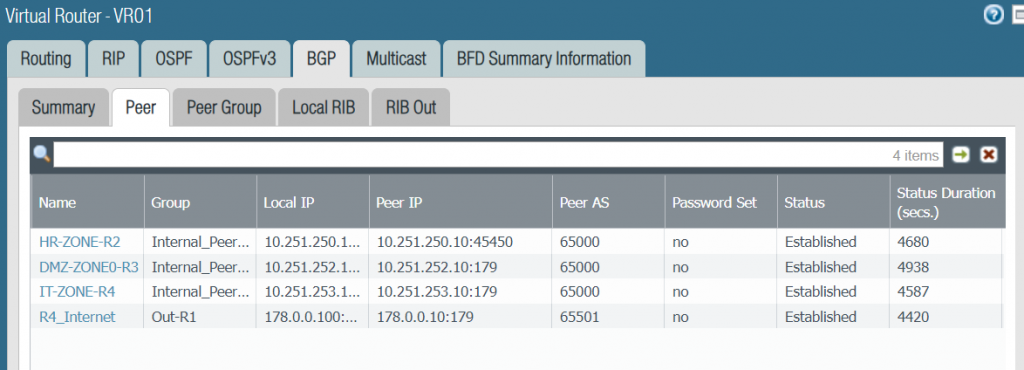
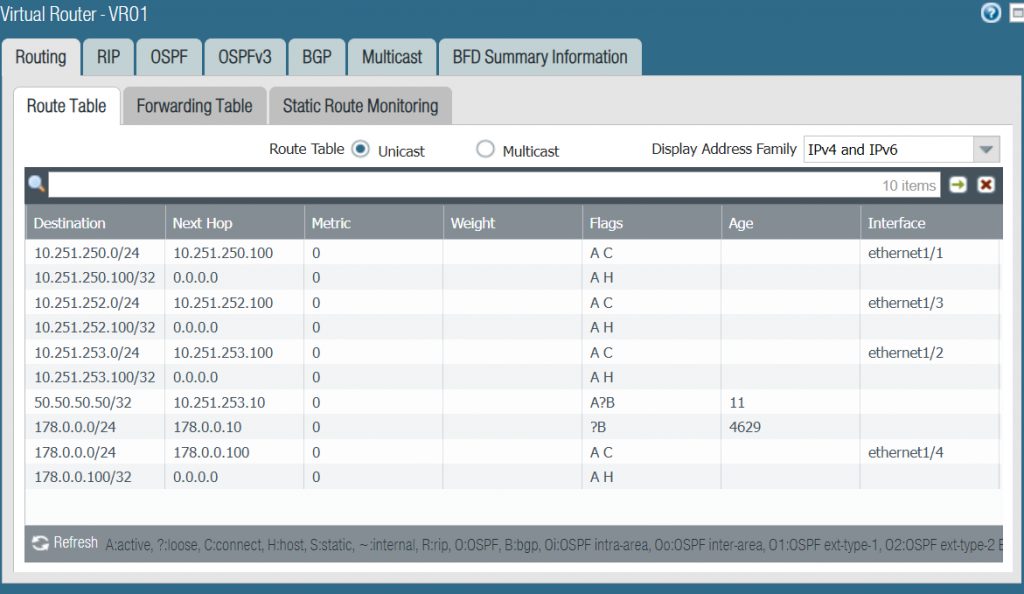
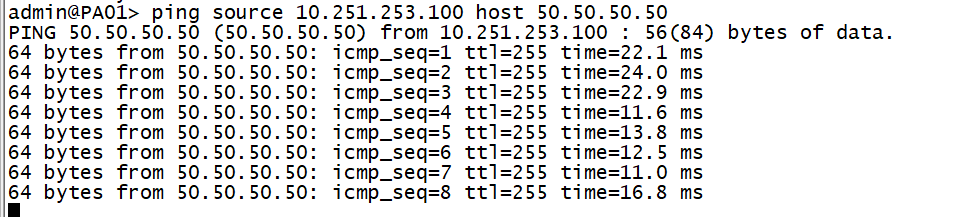
To simulate route learning through BGP on Palo Alto Firewall, we configure a loopback 100 on IT-ZONE-R4 router and advertise it into BGP.
Leave a Reply
You must be logged in to post a comment.
