Implementing GRE over IPsec (ISAKMP mode) on Huawei routers.
- August 25, 2024
- Posted by: James Majani
- Category: Networking
Generic Routing Encapsulation, or GRE, is a protocol for encapsulating data packets that use one routing protocol inside the packets of another protocol. GRE is one way to set up a direct point-to-point connection across a network, for the purpose of simplifying connections between separate networks. It works with a variety of network layer protocols.
IPSec is a suite of protocols and services that provide security for IP networks. It is a widely used Virtual Private Network (VPN) technology. IP packets lack effective security mechanisms and may be forged, stolen, or tampered with when being transmitted on a public network, such as the Internet. To solve this problem, the communicating parties establish an IPsec tunnel for encrypted transmission of IP packets. This ensures secure transmission of IP packets on an insecure network, such as the Internet.
Pros and Cons of Using GRE:
Pros: Highly flexible, can encapsulate a variety of protocols, simplifies the setup of VPNs.
Cons: Lacks built-in security features; susceptible to certain types of cyber attacks if not paired with a security protocol like IPsec.
The Advantages and Limitations of IPsec:
Advantages: Provides comprehensive security measures, supports advanced encryption standards, and is widely adopted in established security frameworks.
Limitations: Can be complex to configure and manage; may incur more overhead than GRE in terms of performance. Another limitation is that it is only IP based offering no flexibility in terms of protocols supported.
While GRE and IPsec can be used separately, combining them leverages the strengths of both technologies. This combination allows for the flexibility of GRE in terms of protocol support alongside the robust security features of IPsec. In this setup, GRE is used to create a tunnel and handle the encapsulation duties, while IPsec is focused on the encryption and integrity of the data passing through that tunnel.
Networking Description.
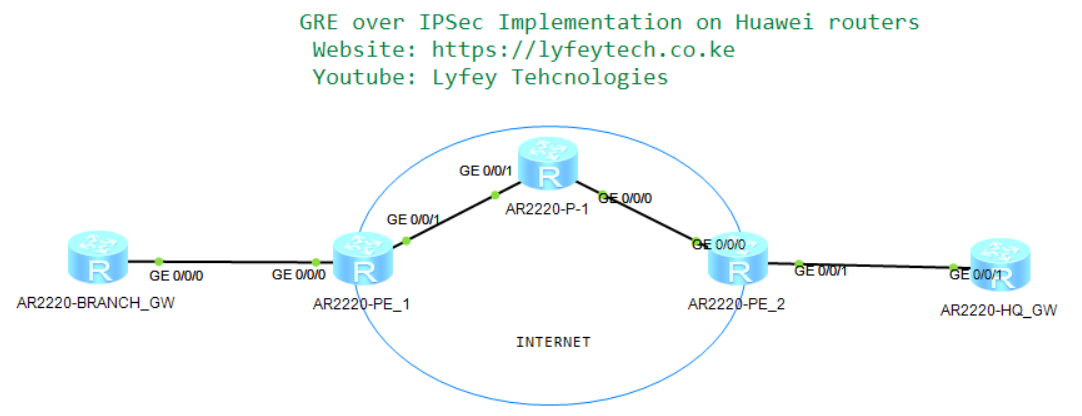
As shown in our topology, HQ router and Branch router, are gateways of the enterprise headquarters and branch. The service provider has allocated a public network IP address to each gateway and the gateways can communicate with each other.
The enterprise requires a highly secure and cost-effective mechanism to implement communication between the headquarters and branches through Internet. GRE over IPSec can be implemented between the headquarters and branches to meet this requirement.
In this environment, BGP and IS-IS is used in the backbone network, between Branch1 and ISP router (PE_1) BGP is used to exchange Public IPS of the gateways across the Internet. For underlay routing, eBGP is deployed between branch/ HQ and respective PEs . For overlay, HQ gateway and Branch gateway exchange LAN-side routes on the GRE tunnel using OSPF. IPSec is deployed on the GRE tunnel between Branch and HQ for secure transmission of data over the internet between the two sites.
Step 1: Basic configurations.
*******************************************AR222_BRANCH_GW
system-view
sysname AR222_BRANCH_GW
#
interface GigabitEthernet0/0/0
ip address 11.1.2.1 255.255.255.254
#
interface LoopBack0
ip address 192.168.2.1 255.255.255.0
#
interface LoopBack1
ip address 192.168.22.1 255.255.255.0
*******************************************AR222_PE_1
system-view
system-view
sysname AR222_PE_1
#
interface GigabitEthernet0/0/0
ip address 11.1.2.0 255.255.255.254
#
interface GigabitEthernet0/0/1
ip address 192.169.1.0 255.255.255.254
*******************************************AR222_P_1
system-view
sysname AR222_P_1
#
interface GigabitEthernet0/0/1
ip address 192.169.1.1 255.255.255.254
#
interface GigabitEthernet0/0/0
ip address 192.169.1.2 255.255.255.254
*******************************************AR222_PE_2
system-view
sysname AR222_PE_2
#
interface GigabitEthernet0/0/0
ip address 192.169.1.3 255.255.255.254
#
interface GigabitEthernet0/0/1
ip address 11.1.1.0 255.255.255.254
*******************************************AR222_HQ_GW
system-view
sysname AR222_HQ_GW
#
interface GigabitEthernet0/0/1
ip address 11.1.1.1 255.255.255.254
ipsec policy P1
#
interface LoopBack0
ip address 192.168.1.1 255.255.255.0
#
interface LoopBack1
ip address 192.168.11.1 255.255.255.0Step 2: Configure routing protocols for route exchange on the underlay.
*******************************************AR222_BRANCH_GW
bgp 65100
peer 11.1.2.0 as-number 64511
#
ipv4-family unicast
undo synchronization
network 11.1.1.0 255.255.255.254
peer 11.1.2.0 enable
*******************************************AR222_PE_1
isis 1
is-level level-1-2
is-name AR222_PE_1
network-entity 49.0001.0000.0000.0001.00
#
interface GigabitEthernet 0/0/0
isis enable 1
#
interface GigabitEthernet 0/0/1
isis enable 1
#
bgp 64511
peer 11.1.2.1 as-number 65100
peer 11.1.1.0 as-number 64511
#
ipv4-family unicast
undo synchronization
import-route direct
peer 11.1.2.1 enable
peer 11.1.1.0 enable
*******************************************AR222_P_1
isis 1
is-level level-1-2
is-name AR222_P_1
network-entity 49.0001.0000.0000.0002.00
#
interface GigabitEthernet 0/0/0
isis enable 1
#
interface GigabitEthernet 0/0/1
isis enable 1
*******************************************AR222_PE_2
isis 1
is-level level-1-2
is-name AR222_PE_2
network-entity 49.0001.0000.0000.0001.00
#
interface GigabitEthernet 0/0/0
isis enable 1
#
interface GigabitEthernet 0/0/1
isis enable 1
#
bgp 64511
peer 11.1.1.1 as-number 65100
peer 11.1.2.0 as-number 64511
#
ipv4-family unicast
undo synchronization
import-route direct
peer 11.1.1.1 enable
peer 11.1.2.0 enable
#
*******************************************AR222_HQ_GW
bgp 65100
peer 11.1.1.0 as-number 64511
#
ipv4-family unicast
undo synchronization
peer 11.1.1.0 enable
network 11.1.1.0 255.255.255.254Results confirmation.
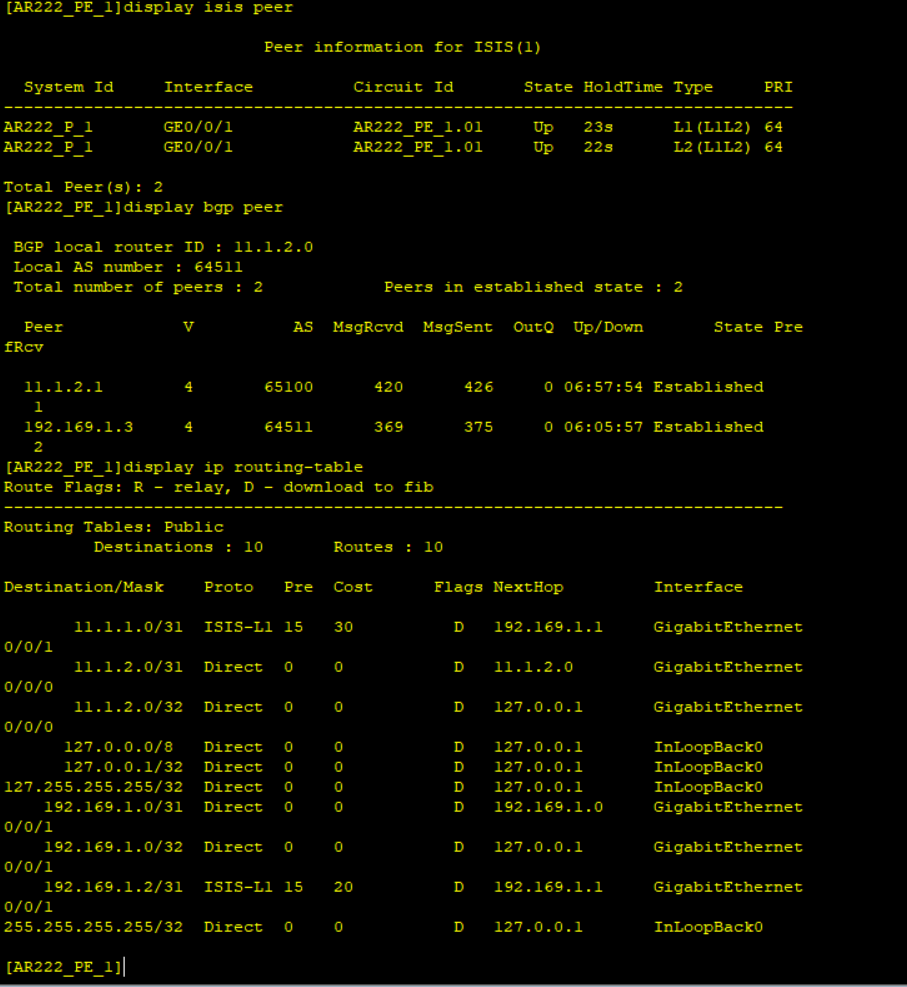
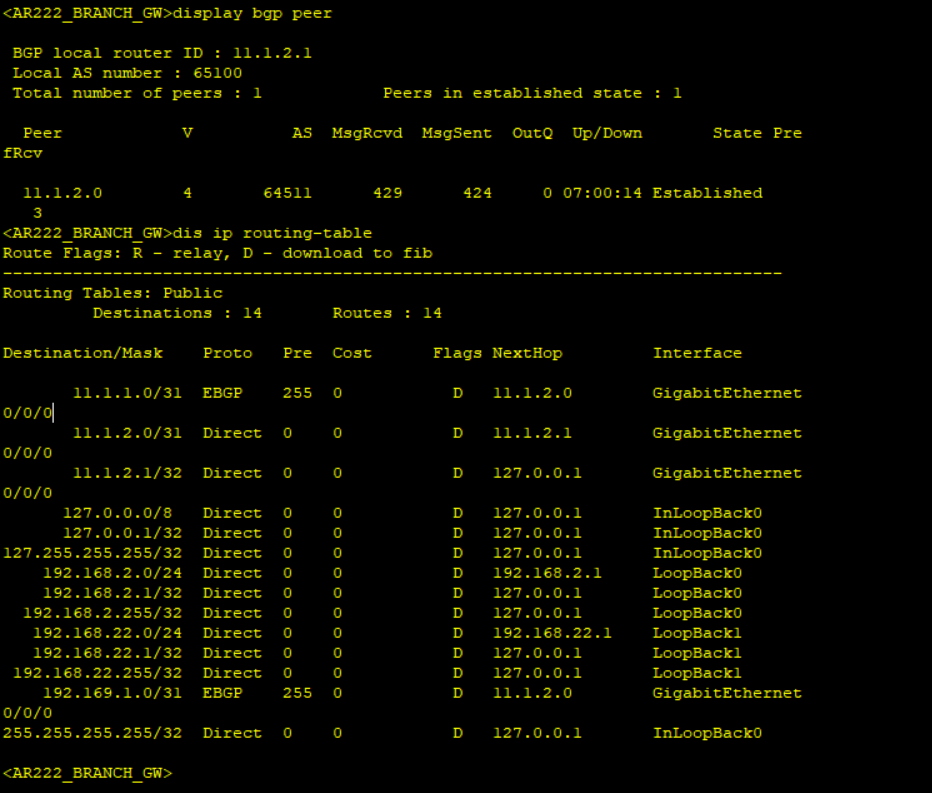
It’s confirmed that the routing protocols states are as expected and the Branch GW is learning the public IP address of the HQ gateway and vice versa.
Step 3: Create overlay VPN instance and bind the overlay service to the VPN instance.
*******************************************AR222_BRANCH_GW
ip vpn-instance VRFB
ipv4-family
route-distinguisher 21:21
vpn-target 21:21 both
#
interface LoopBack0
ip binding vpn-instance VRFB
ip address 192.168.2.1 255.255.255.0
#
interface LoopBack1
ip binding vpn-instance VRFB
ip address 192.168.22.1 255.255.255.0
*******************************************AR222_HQ_GW
ip vpn-instance VRFA
ipv4-family
route-distinguisher 12:12
vpn-target 21:21 both
#
interface LoopBack0
ip binding vpn-instance VRFA
ip address 192.168.1.1 255.255.255.0
#
interface LoopBack1
ip binding vpn-instance VRFA
ip address 192.168.11.1 255.255.255.0
Step 4: Create GRE tunnels and add them to respective VRFs.
*******************************************AR222_BRANCH_GW
interface tunnel 0/0/0
ip binding vpn-instance VRFB
tunnel-protocol gre
ip address 172.16.2.2 26
source 11.1.2.1
destination 11.1.1.1
*******************************************AR222_HQ_GW
interface tunnel 0/0/0
ip binding vpn-instance VRFA
tunnel-protocol gre
ip address 172.16.2.1 26
source 11.1.1.1
destination 11.1.2.1Results confirmation.
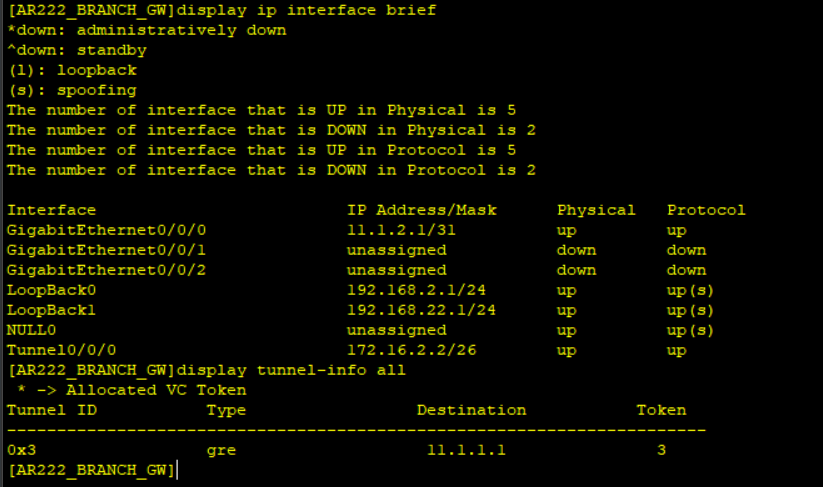
Step 5: Configure IPSec parameters and bind the IPSec profile to the GRE tunnel interface.
*******************************************AR222_BRANCH_GW
IPsec proposal PRP1
transform esp
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-128
encapsulation-mode tunnel
#
Ike proposal 1
authentication-algorithm sha1
encryption-algorithm aes-cbc-128
dh group14
#
Ike peer peer1 v2
peer-id-type
pre-shared-key cipher Huawei@123
ike proposal 1
#
IPsec profile PRF1
ike-peer peer1
proposal PRP1
#
interface tunnel 0/0/0
IPsec profile PRF1
*******************************************AR222_HQ_GW
IPsec proposal PRP1
transform esp
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-128
encapsulation-mode tunnel
#
Ike proposal 1
authentication-algorithm sha1
encryption-algorithm aes-cbc-128
dh group14
#
Ike peer peer1 v2
peer-id-type
pre-shared-key cipher Huawei@123
ike proposal 1
#
IPsec profile PRF1
ike-peer peer1
proposal PRP1
#
interface tunnel 0/0/0
IPsec profile PRF1 Step 6: Configure OSPF over the tunnels.
*******************************************AR222_BRANCH_GW
ospf 1 router-id 2.2.2.2 vpn-instance VRFB
area 0.0.0.0
network 172.16.2.0 0.0.0.63
network 192.168.2.0 0.0.0.255
network 192.168.22.0 0.0.0.255
*******************************************AR222_HQ_GW
ospf 1 router-id 1.1.1.1 vpn-instance VRFA
area 0.0.0.0
network 172.16.2.0 0.0.0.63
network 192.168.1.0 0.0.0.255
network 192.168.11.0 0.0.0.255
Results confirmation.
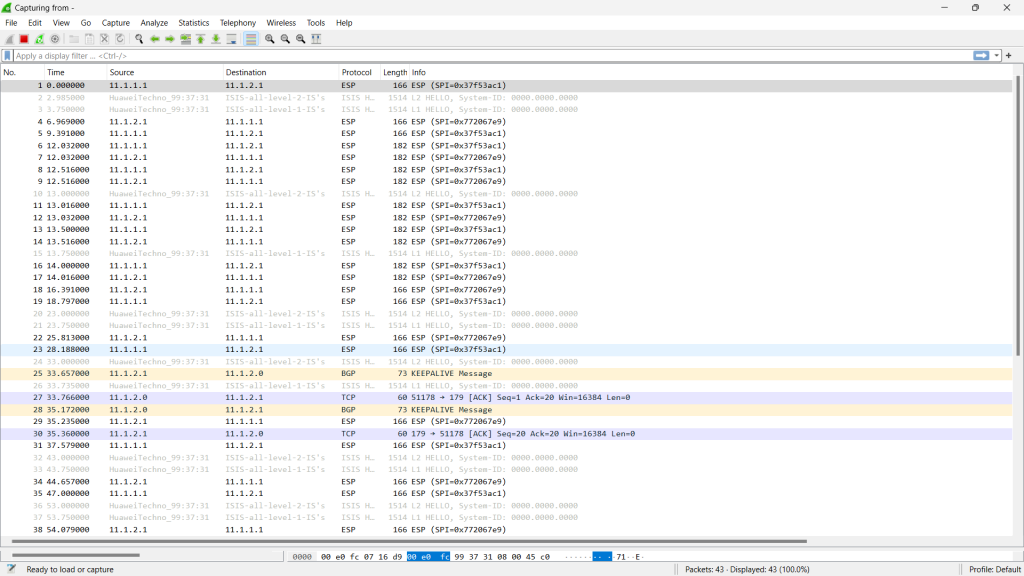
A packet capture done on interface GigabitEthernet 0/0/0 of AR222_BRANCH_GW
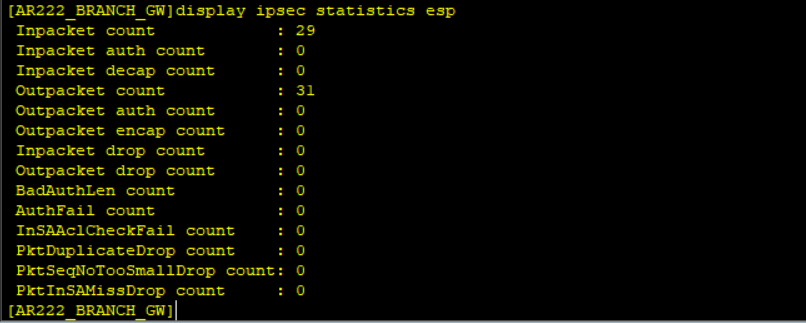
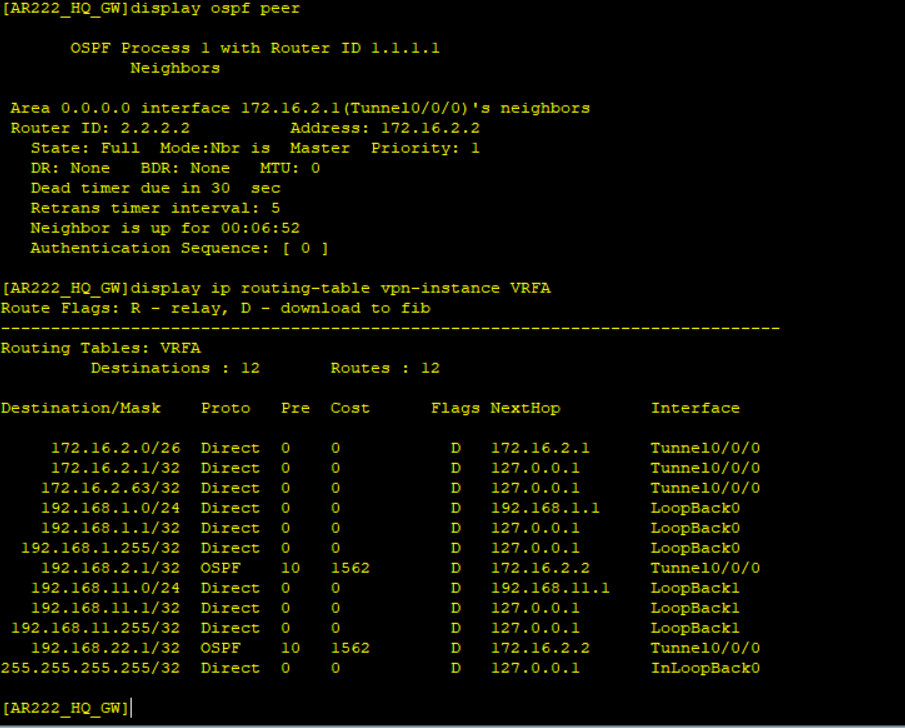
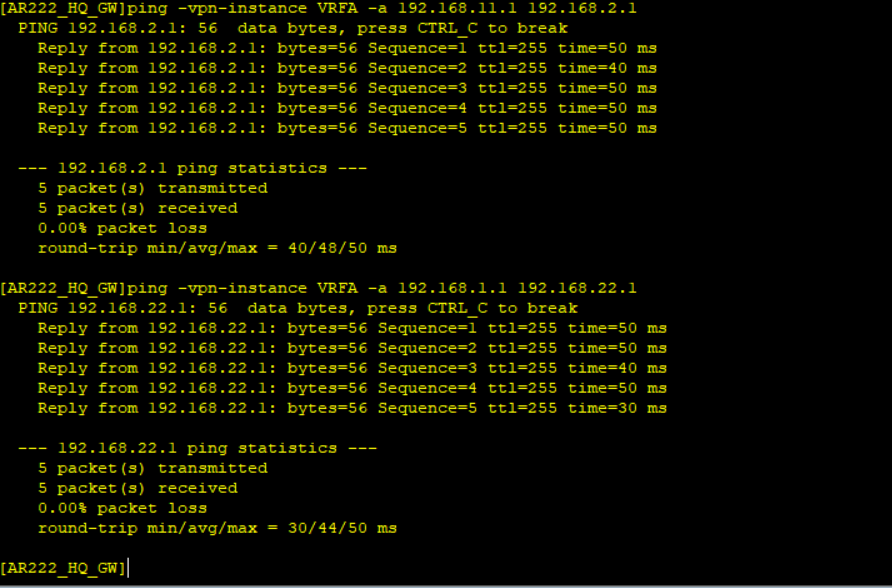
The two sites have exchanged routes via a secure GRE over IPSec tunnel and LAN side routes of the two sites are reachable over the tunnel.
Leave a Reply
You must be logged in to post a comment.
