Dual Link HSB (Direct forwarding) Implementation on Huawei WACs.
- November 10, 2024
- Posted by: James Majani
- Category: Networking
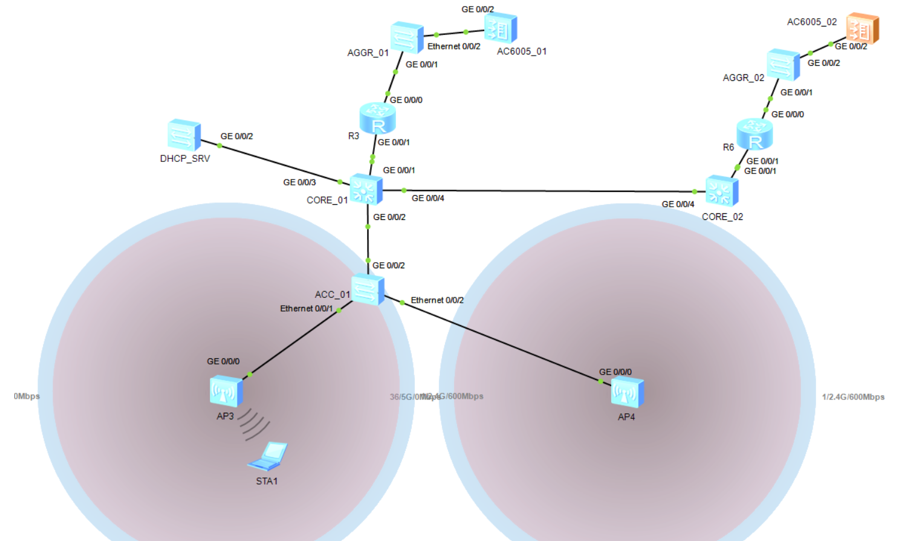
Dual-link hot standby (HSB) ensures high reliability by preventing STA network access from being affected by failures of an AC or CAPWAP links. The active and standby ACs are bound to the HSB service. The HSB channel created based on the HSB service is used to back up STA entries, ensuring service continuity during an active/standby switchover or switchback. Synchronization modes include batch, real-time, and periodic backup.
Networking description.
Two ACs are deployed in active/standby mode. The GW of AP’s management and wireless users is on the CORE_01. VLAN100 is AP management VLAN while VLAN 101 is service VLAN. Configure Dual link HSB is on AC1 and AC2, set AC1 as the active device to forward traffic. Configure HSB service on the ACs so that service information on AC1 is backed up to AC2 ensuring seamless service switchover when the active AC fails.
Step 1: Configure access switch DHCP server, core switches, aggregation switches and ARs.
*******************************************ACC_01
system-view
sysname ACC_01
#
vlan batch 100 to 101
#
interface Ethernet0/0/1
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 to 101
#
interface Ethernet0/0/2
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 to 101
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 100 to 101
#
return
*******************************************DHCP_SRV
system-view
sysname DHCP_SRV
#
vlan batch 100 to 101
#
ip pool ap_management
gateway-list 10.23.100.1
network 10.23.100.0 mask 255.255.255.0
excluded-ip-address 10.23.100.2 10.23.100.9
option 43 sub-option 1 ip-address 10.23.104.1 10.23.204.1
#
ip pool wireless_users
gateway-list 10.23.101.1
network 10.23.101.0 mask 255.255.255.0
excluded-ip-address 10.23.101.2 10.23.101.10
dns-list 10.23.101.1
#
interface Vlanif100
ip address 10.23.100.5 255.255.255.0
dhcp select global
#
interface Vlanif101
ip address 10.23.101.5 255.255.255.0
dhcp select global
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 100 to 101
#
return
*******************************************CORE_01
system-view
sysname CORE_01
#
vlan batch 100 to 103 199
#
interface Vlanif100
ip address 10.23.100.1 255.255.255.0
#
interface Vlanif101
ip address 10.23.101.1 255.255.255.0
#
interface Vlanif103
ip address 10.23.103.1 255.255.255.252
#
interface Vlanif199
ip address 10.0.0.1 255.255.255.252
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk pvid vlan 103
port trunk allow-pass vlan 100 to 101 103
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 100 to 101
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 100 to 101
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk allow-pass vlan 199
#
ospf 1
default-route-advertise always type 2
import-route static type 2
area 0.0.0.0
network 10.23.103.0 0.0.0.3
network 10.23.105.0 0.0.0.3
network 10.0.0.0 0.0.0.3
network 10.23.100.0 0.0.0.255
network 10.23.101.0 0.0.0.255
#
return
*******************************************CORE_02
system-view
sysname CORE_2
#
vlan batch 199 203
#
interface Vlanif199
ip address 10.0.0.2 255.255.255.252
#
interface Vlanif203
ip address 10.23.203.1 255.255.255.252
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 203
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk allow-pass vlan 199
#
ospf 1
area 0.0.0.0
network 10.0.0.0 0.0.0.3
network 10.23.203.0 0.0.0.3
#
return
*******************************************R3
system-view
sysname R3
#
vlan batch 103 to 104
#
interface Vlanif104
ip address 10.23.104.2 255.255.255.252
#
interface GigabitEthernet0/0/0
portswitch
port link-type trunk
port trunk allow-pass vlan 104
#
interface GigabitEthernet0/0/1
mac-address 5489-9833-8442
ip address 10.23.103.2 255.255.255.252
#
ip route-static 10.0.0.0 255.255.255.252 10.23.103.1
ip route-static 10.23.0.0 255.255.0.0 10.23.103.1
ip route-static 10.23.203.0 255.255.255.252 10.23.103.1
#
return
*******************************************R6
system-view
sysname R6
#
vlan batch 203 to 204
#
interface Vlanif203
ip address 10.23.203.2 255.255.255.252
#
interface Vlanif204
ip address 10.23.204.2 255.255.255.252
#
interface GigabitEthernet0/0/0
portswitch
port link-type trunk
port trunk allow-pass vlan 204
#
interface GigabitEthernet0/0/1
portswitch
port link-type trunk
port trunk allow-pass vlan 203
#
ospf 1
area 0.0.0.0
network 10.23.204.0 0.0.0.3
network 10.23.203.0 0.0.0.3
#
return
*******************************************AGGR_01
system-view
sysname AGGR_01
#
vlan batch 104
#
interface Ethernet0/0/2
port link-type trunk
port trunk allow-pass vlan 104
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 104
#
return
*******************************************AGGR_02
system-view
sysname AGG_02
#
vlan batch 204
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 204
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 204
#
port-group 1
group-member GigabitEthernet0/0/1
group-member GigabitEthernet0/0/2
#
return
Step 2: Configure basic and Wi-Fi parameters and specify CAPWAP source.
*******************************************AC6005_01
system-view
sysname AC6005_01
#
interface Vlanif104
ip address 10.23.104.1 255.255.255.252
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 104
#
ip route-static 10.0.0.0 255.255.255.252 10.23.104.2
ip route-static 10.23.0.0 255.255.0.0 10.23.104.2
ip route-static 10.23.203.0 255.255.255.252 10.23.104.2
ip route-static 10.23.204.0 255.255.255.252 10.23.104.2
#
capwap source interface vlanif104
#
wlan
security-profile name MVP
security wpa-wpa2 psk pass-phrase jambo_987 aes
ssid-profile name MVP
ssid MVP
vap-profile name MVP
service-vlan vlan-id 101
ssid-profile MVP
security-profile MVP
regulatory-domain-profile name MVP
country-code CH
ap-group name MVP
regulatory-domain-profile MVP
radio 0
vap-profile MVP wlan 1 radio all
ap auth-mode mac-auth
ap-id 0 type-id 69 ap-mac 00e0-fc54-0cb0 ap-sn 210235448310442C5C35
ap-name AP2
ap-group MVP
ap-id 3 type-id 69 ap-mac 00e0-fc69-4b90 ap-sn 210235448310E238D720
ap-name AP1
ap-group MVP
provision-ap
*******************************************AC6005_02
system-view
sysname AC6005_02
#
vlan batch 204
#
interface Vlanif204
ip address 10.23.204.1 255.255.255.252
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 204
#
ospf 1
area 0.0.0.0
network 10.23.204.1 0.0.0.0
#
capwap source interface vlanif204
#
wlan
security-profile name MVP
security wpa-wpa2 psk pass-phrase jambo_987 aes
ssid-profile name MVP
ssid MVP
vap-profile name MVP
service-vlan vlan-id 101
ssid-profile MVP
security-profile MVP
regulatory-domain-profile name MVP
country-code CH
ap-group name MVP
regulatory-domain-profile MVP
radio 0
vap-profile MVP wlan 1 radio all
ap auth-mode mac-auth
ap-id 0 type-id 69 ap-mac 00e0-fc54-0cb0 ap-sn 210235448310442C5C35
ap-name AP2
ap-group MVP
ap-id 3 type-id 69 ap-mac 00e0-fc69-4b90 ap-sn 210235448310E238D720
ap-name AP1
ap-group MVP
provision-apStep 3: Configure HSB service for the two WACs.*******************************************AC6005_01
hsb-service 0
service-ip-port local-ip 10.23.104.1 peer-ip 10.23.204.1 local-data-port 10555
peer-data-port 10555
#
hsb-service-type access-user hsb-service 0
#
hsb-service-type ap hsb-service 0
#
*******************************************AC6005_02
hsb-service 0
service-ip-port local-ip 10.23.204.1 peer-ip 10.23.104.1 local-data-port 10555
peer-data-port 10555
#
hsb-service-type access-user hsb-service 0
#
hsb-service-type ap hsb-service 0
#Step 4: Enable AC protection and specify active and standby WAC under ap-system profile view.
*******************************************AC6005_01
wlan
ac protect enable
ap-system-profile name default
primary-access ip-address 10.23.104.1
backup-access ip-address 10.23.204.1
*****************************************2*AC6005_01
wlan
ac protect enable
ap-system-profile name default
primary-access ip-address 10.23.104.1
backup-access ip-address 10.23.204.1Step 5: Result verification.
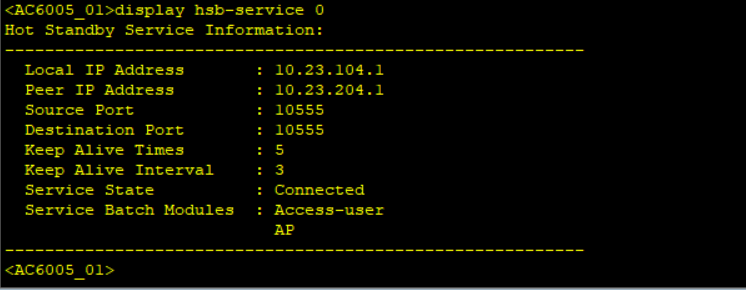
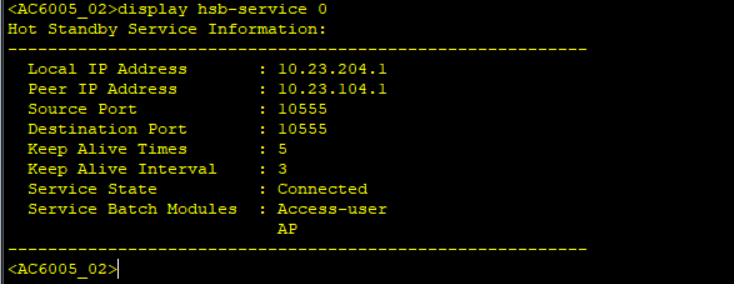
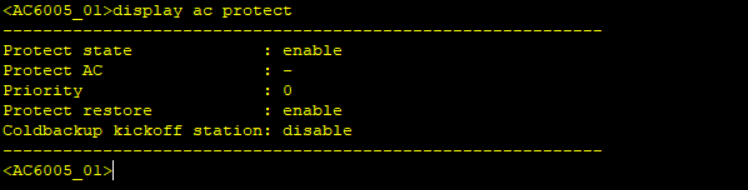
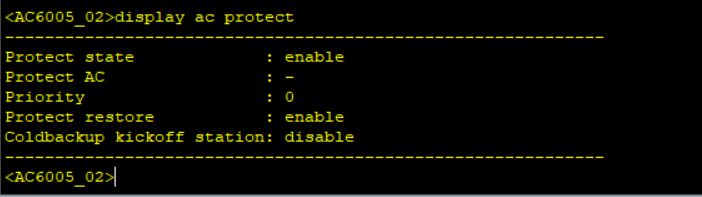
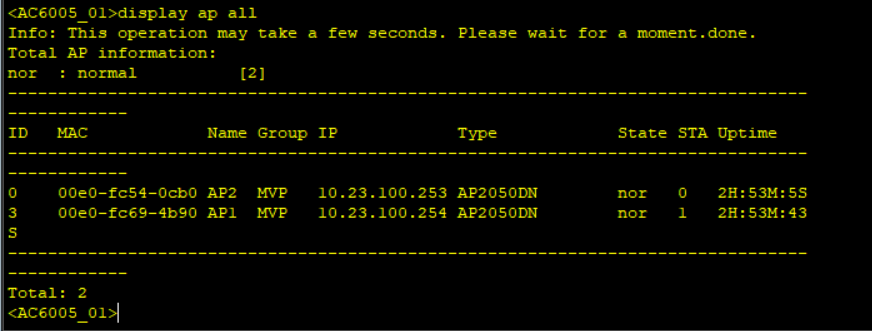
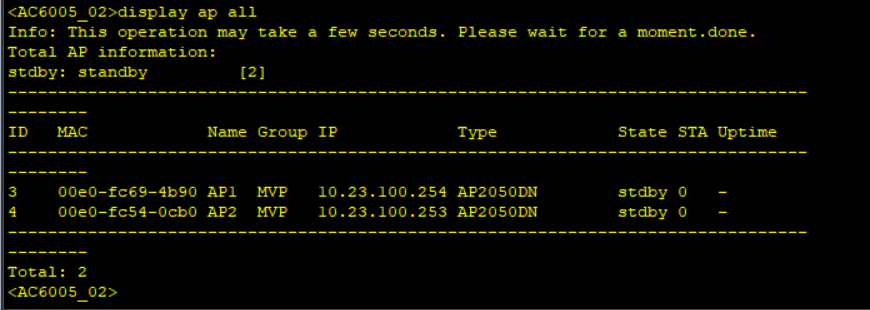
Simulate a failover and check AP status on the two WAC, shutdown the Capwap source interface.
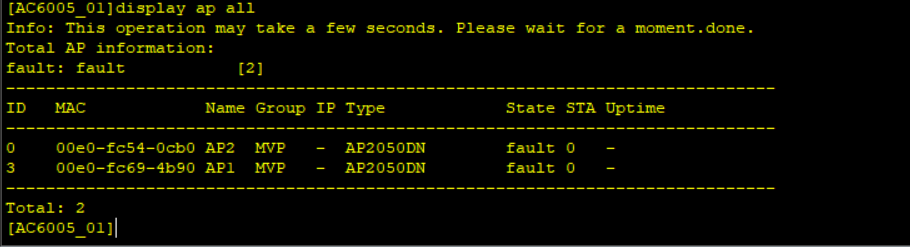
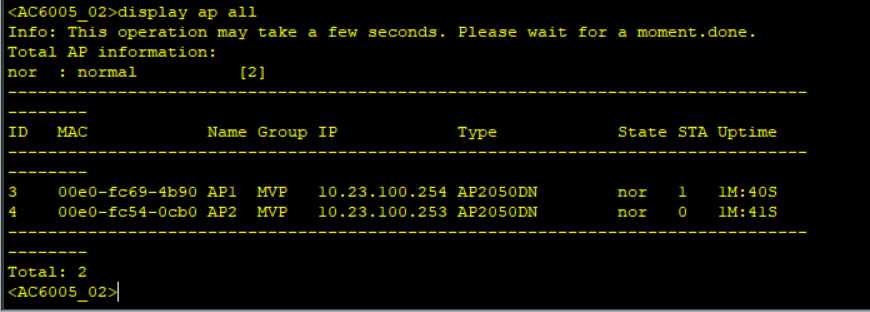
When the link is faulty, the AC cannot respond to Echo messages from the AP. If the active AC does not respond after the specified number of CAPWAP heartbeat detections in the CAPWAP heartbeat interval, the AP determines that the primary tunnel has failed.
The AP sends an Echo Request message carrying information about the active AC to the standby AC. After receiving the Echo Request message, the standby AC switches to the working state, and the AP sends STA data to the standby AC.
Check our Latest Posts
- Step by step guide on how to implement different networking protocols on Juniper MX routers
- L2 EVPN Implementation on Huawei Routers.
- VRRP Monitoring of the Uplink Interface status on Huawei routers.
- Association between VRRP and BFD Implementation on Huawei routers.
- Association between VRRP and STP Implementation on Huawei routers.
Visit our YouTube channel: https://www.youtube.com/@LyfeyTechnologies
Leave a Reply
You must be logged in to post a comment.
